ALAN ZISMAN ON
TECHNOLOGY
Has this happened to you?
By Alan Zisman © July 8 2013
This morning, I received an email, apparently from 'Alex' - a guy who I know casually but haven't spoken with - in person or digitally - in a couple of years.
I hope you don't take offense in my sudden approach for help. I took a
trip to Limassol, Cyprus and was attacked and robbed. My belongings
including my cash, credit card and cell phones were all stolen. I've
made contact with my bank but the best they can do is to mail me a new
card which will take 7 working days to arrive here, am currently
concluding my documentation at the embassy so i can fly out. I need
you to lend me some funds to settle some bills.
Please let me know if you can assist me in anyway so i can forward you
details to effect a transfer. Waiting for your mail.
Thanks
What would you do? Me, I was skeptical.
Like I said, I haven't spoken to Alex in quite a while - I'd be surprised if I was someone he would pick to approach for help. And there's nothing personal in the message - my name doesn't appear, not anything about Alex, nothing that would let me know that this is really a message from the guy I know to me. It screams 'scam'.
Here's my reply:
Alex - if this is a legitimate email, you have my sympathy.
Unfortunately, it sounds like an all too common Internet scam - if that's the case, you should -
- change your email password now, without delay!
- notify all your email contacts that you're okay and to ignore the scam message
- check your computer for malware
A week ago I gave a talk at the Kiwanis Internation 2013 convention, held in Vancouver, on the topic of 'Protecting Your Internet Identity'. (Presentation available online). This email would have fit right in, along with the more common email messages from strangers or apparently from folks you know urging you to click a link - to see a video or a document or just for no reason at all. Or the ones from PayPal or a bank requesting you click to log in to fix a problem with your account.
Or the phone call claiming to be from Microsoft telling you that they have noticed that your computer was infected with malware. Or the Facebook message - again apparently from a friend - giving you a link to a video... but if you click it no video appears.
One more - you've enjoyed playing the limited free version of a game on your Android phone but don't want to pay $5.99 for the full version. A Google search shows that you can download a full version of the game for free - or maybe you even found the free full version on Google's Android Play Store.
All examples of current crop of Internet scams and malware.
Some things to note:
A useful trick - if you hover your mouse over a link, you can often see the link's target, perhaps at the bottom of the browser window, perhaps as a pop-up above (or below) the link. Does the link reading 'Log into Paypal' really point to paypal.com? Check before you click!
But scammers, knowing that, can try to embed a real-looking URL (Internet address) within a long scammy one:
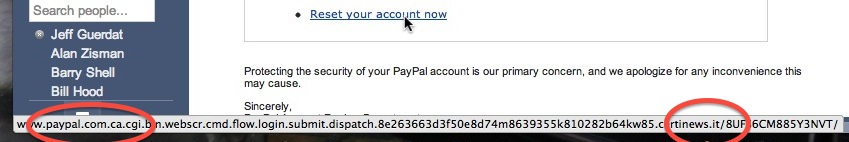
Notice how the long link that ends at some website in Italy (something.it) starts with www.paypal.com.
Your first line of defense is your password - if you think anything suspicious has happened to any of your many accounts, the first thing you should do is change its password. Use different passwords for different accounts (and don't write them on a sticky note attached to your screen!). Since you're going to end up with lots of different passwords, consider storing them in a password manager - either a utility on your computer or an online service like LastPass.
Many services are offering optional 2-Factor Authentication. If available, enable it. With this, if you - or someone else - try to log onto the service from a new device, a code is sent in a text message to your mobile phone. You have to enter that code in order to log in. This can be very effective in keeping scammers from being able to use your accounts from their computers. For more on this, see: http://securitywatch.pcmag.com/apps-and-websites/313340-how-to-turn-on-two-factor-authentication-for-your-email
 Update
your operating system, applications, browser add-ons, etc. It's a pain,
but when you see the update notification just do it. Putting it off
doesn't help! Windows users may want to set up the free Secunia PSI update
manager. Windows, Mac, and Android users should all have
antivirus/antimalware software installed and up to date. (The antivirus
that was running when you bought your computer was a trial version that
was good for 90-days or so; after that you needed to buy it to keep it
current. If you did, fine. Otherwise there are lots of good free
antivirus software available for the various platforms. I'm using the
free Avast on my Macs, Sophos on my Android devices, and Microsoft
Security Essentials on my Windows systems - but there are other good -
and free - alternatives).
Update
your operating system, applications, browser add-ons, etc. It's a pain,
but when you see the update notification just do it. Putting it off
doesn't help! Windows users may want to set up the free Secunia PSI update
manager. Windows, Mac, and Android users should all have
antivirus/antimalware software installed and up to date. (The antivirus
that was running when you bought your computer was a trial version that
was good for 90-days or so; after that you needed to buy it to keep it
current. If you did, fine. Otherwise there are lots of good free
antivirus software available for the various platforms. I'm using the
free Avast on my Macs, Sophos on my Android devices, and Microsoft
Security Essentials on my Windows systems - but there are other good -
and free - alternatives).
Don't ever (ever!) though install antivirus software 'recommended' by a mystery pop-up message on your computer! That software is typically malware that can freeze your computer and hold it for ransom until you pay a fee to uninstall it. Not sure? Check reviews from a trustworthy source, such as PC Magazine's Best Antivirus for 2013. As a second line of defense you can use an online virus-checker such as Trend Micro's Housecall.
Be especially wary at public-access computers such as web cafes - someone may have installed key-logger software to capture your log-in information. Similarly, be wary of 'free' wi-fi services: it's easy for someone sitting nearby to create a wi-fi network, name it 'Free Wi-Fi' and capture the data you send. Rule of thumb: don't do online banking or credit card purchases on public computers and free wi-fi networks.
If you're using public-access computer be sure to uncheck the 'safe your password' option when logging into email, social networks, and other password-accessed websites. And be sure to log-out when leaving those sites - closing the browser window isn't good enough: the next person at that computer may have access to your identity. It may not be clear how to log out of many services - here are screen captures for Gmail and Facebook:

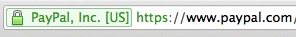
Whether at a public-access computer or at home, when accessing a bank or an online vendor (or any other website where you might be sending confidential information) check to see whether the address starts with 'https' ('s' for secure) rather than the standard 'http' and look for a little padlock icon; both indicate that any information that you send will be encrypted.
And be careful letting your credit card number be saved by smaller, perhaps sketchier, retail sites - better to let major services like PayPal or Amazon store your information and then temporarily save it with smaller sites as needed.
Set your smartphone, tablet, and notebook so the screen is locked when it's been unused for a few moments - while it's a minor pain to have to enter a code before you use the device again, it will help keep your accounts from being accessed if the device is lost or stolen. (I've found three mobile phones in the last couple of years including an iPhone in the middle of the road!)
Android users: be careful installing apps from sources other than Google's Play Store - and even there, be wary of apps promising to be free versions of paid apps. Take a moment to check the Permissions list when you install an app and think critically - does that game really need to be able to send text messages? Why does it want access to your contacts?
Do I sound like your mother here? The key message to take away is to think critically online - never trust strangers, especially those offering the online equivalent of candy. Think before you click!
Older blog postings....
Has this happened to you?
By Alan Zisman © July 8 2013
This morning, I received an email, apparently from 'Alex' - a guy who I know casually but haven't spoken with - in person or digitally - in a couple of years.
I hope you don't take offense in my sudden approach for help. I took a
trip to Limassol, Cyprus and was attacked and robbed. My belongings
including my cash, credit card and cell phones were all stolen. I've
made contact with my bank but the best they can do is to mail me a new
card which will take 7 working days to arrive here, am currently
concluding my documentation at the embassy so i can fly out. I need
you to lend me some funds to settle some bills.
Please let me know if you can assist me in anyway so i can forward you
details to effect a transfer. Waiting for your mail.
Thanks
What would you do? Me, I was skeptical.
Like I said, I haven't spoken to Alex in quite a while - I'd be surprised if I was someone he would pick to approach for help. And there's nothing personal in the message - my name doesn't appear, not anything about Alex, nothing that would let me know that this is really a message from the guy I know to me. It screams 'scam'.
Here's my reply:
Alex - if this is a legitimate email, you have my sympathy.
Unfortunately, it sounds like an all too common Internet scam - if that's the case, you should -
- change your email password now, without delay!
- notify all your email contacts that you're okay and to ignore the scam message
- check your computer for malware
A week ago I gave a talk at the Kiwanis Internation 2013 convention, held in Vancouver, on the topic of 'Protecting Your Internet Identity'. (Presentation available online). This email would have fit right in, along with the more common email messages from strangers or apparently from folks you know urging you to click a link - to see a video or a document or just for no reason at all. Or the ones from PayPal or a bank requesting you click to log in to fix a problem with your account.
Or the phone call claiming to be from Microsoft telling you that they have noticed that your computer was infected with malware. Or the Facebook message - again apparently from a friend - giving you a link to a video... but if you click it no video appears.
One more - you've enjoyed playing the limited free version of a game on your Android phone but don't want to pay $5.99 for the full version. A Google search shows that you can download a full version of the game for free - or maybe you even found the free full version on Google's Android Play Store.
All examples of current crop of Internet scams and malware.
Some things to note:
- At one time, computer viruses were the digital equivalent of graffiti and tagging - something that individual hackers did to show off their skills to their peers. That hasn't been the case for a while. All the examples above are about money - install the Android malware, for instance, and you may find that your phone starts quietly sending 'Premium SMS' text messages, billing your mobile account. Your computer may end up with key logging software installed watching everything you type looking for credit card and bank account information. Or your infected computer may become part of a 'botnet' - a network of infected computers serving up spam (or scam) emailmessages to others.
- Some types of systems are more vulnerable than others. Windows has long been a target, with XP more vulnerable than Windows 7 or 8. Macs are no invulnerable - though there are very few examples of Mac malware 'in the wild'. iOS devices: iPhones, iPads and iPod Touch devices are not currently being targetted, but Android phones and tablets have seen a 600% increase in malware from 2012 to 2013.
- Vulnerabilities in applications and browser add-ins are increasingly being targetted,
rather than holes in operating systems: Adobe Reader and Flash and Java
for example. This has the potential of being a problem for Mac users as
well as Windows users.
- Along with Android devices, social networks - particularly Facebook - are where malware is moving.
- Spam, phishing, and other scams can affect people regardless of what they are using - Windows, Mac, iPhone, Android, or what-have-you... if you give your bank log on information at a fraudulent website your bank account can be emptied.
A useful trick - if you hover your mouse over a link, you can often see the link's target, perhaps at the bottom of the browser window, perhaps as a pop-up above (or below) the link. Does the link reading 'Log into Paypal' really point to paypal.com? Check before you click!
But scammers, knowing that, can try to embed a real-looking URL (Internet address) within a long scammy one:

Notice how the long link that ends at some website in Italy (something.it) starts with www.paypal.com.
Your first line of defense is your password - if you think anything suspicious has happened to any of your many accounts, the first thing you should do is change its password. Use different passwords for different accounts (and don't write them on a sticky note attached to your screen!). Since you're going to end up with lots of different passwords, consider storing them in a password manager - either a utility on your computer or an online service like LastPass.
Many services are offering optional 2-Factor Authentication. If available, enable it. With this, if you - or someone else - try to log onto the service from a new device, a code is sent in a text message to your mobile phone. You have to enter that code in order to log in. This can be very effective in keeping scammers from being able to use your accounts from their computers. For more on this, see: http://securitywatch.pcmag.com/apps-and-websites/313340-how-to-turn-on-two-factor-authentication-for-your-email
 Update
your operating system, applications, browser add-ons, etc. It's a pain,
but when you see the update notification just do it. Putting it off
doesn't help! Windows users may want to set up the free Secunia PSI update
manager. Windows, Mac, and Android users should all have
antivirus/antimalware software installed and up to date. (The antivirus
that was running when you bought your computer was a trial version that
was good for 90-days or so; after that you needed to buy it to keep it
current. If you did, fine. Otherwise there are lots of good free
antivirus software available for the various platforms. I'm using the
free Avast on my Macs, Sophos on my Android devices, and Microsoft
Security Essentials on my Windows systems - but there are other good -
and free - alternatives).
Update
your operating system, applications, browser add-ons, etc. It's a pain,
but when you see the update notification just do it. Putting it off
doesn't help! Windows users may want to set up the free Secunia PSI update
manager. Windows, Mac, and Android users should all have
antivirus/antimalware software installed and up to date. (The antivirus
that was running when you bought your computer was a trial version that
was good for 90-days or so; after that you needed to buy it to keep it
current. If you did, fine. Otherwise there are lots of good free
antivirus software available for the various platforms. I'm using the
free Avast on my Macs, Sophos on my Android devices, and Microsoft
Security Essentials on my Windows systems - but there are other good -
and free - alternatives).Don't ever (ever!) though install antivirus software 'recommended' by a mystery pop-up message on your computer! That software is typically malware that can freeze your computer and hold it for ransom until you pay a fee to uninstall it. Not sure? Check reviews from a trustworthy source, such as PC Magazine's Best Antivirus for 2013. As a second line of defense you can use an online virus-checker such as Trend Micro's Housecall.
Be especially wary at public-access computers such as web cafes - someone may have installed key-logger software to capture your log-in information. Similarly, be wary of 'free' wi-fi services: it's easy for someone sitting nearby to create a wi-fi network, name it 'Free Wi-Fi' and capture the data you send. Rule of thumb: don't do online banking or credit card purchases on public computers and free wi-fi networks.
If you're using public-access computer be sure to uncheck the 'safe your password' option when logging into email, social networks, and other password-accessed websites. And be sure to log-out when leaving those sites - closing the browser window isn't good enough: the next person at that computer may have access to your identity. It may not be clear how to log out of many services - here are screen captures for Gmail and Facebook:


Whether at a public-access computer or at home, when accessing a bank or an online vendor (or any other website where you might be sending confidential information) check to see whether the address starts with 'https' ('s' for secure) rather than the standard 'http' and look for a little padlock icon; both indicate that any information that you send will be encrypted.

And be careful letting your credit card number be saved by smaller, perhaps sketchier, retail sites - better to let major services like PayPal or Amazon store your information and then temporarily save it with smaller sites as needed.
Set your smartphone, tablet, and notebook so the screen is locked when it's been unused for a few moments - while it's a minor pain to have to enter a code before you use the device again, it will help keep your accounts from being accessed if the device is lost or stolen. (I've found three mobile phones in the last couple of years including an iPhone in the middle of the road!)
Android users: be careful installing apps from sources other than Google's Play Store - and even there, be wary of apps promising to be free versions of paid apps. Take a moment to check the Permissions list when you install an app and think critically - does that game really need to be able to send text messages? Why does it want access to your contacts?
Do I sound like your mother here? The key message to take away is to think critically online - never trust strangers, especially those offering the online equivalent of candy. Think before you click!
Older blog postings....
| About This Blog... I've been writing about computers, software, Internet and the rest of technology since 1992, including a 17 year (1995-2012) stint as 'High Tech Office' columnist for Business in Vancouver. This blog includes thoughts on technology, society, and anything else that might interest me. Comments, emailed to alan@zisman.ca are welcome - and may be published in whole or part. You can follow me on Twitter for notice of new blog postings. |
 |